
It took just one year for the cybersecurity landscape to change dramatically.
As organizations large and small adapted to social distancing guidelines by embracing remote work arrangements as the new normal, cybercriminals shifted their sights to individual employees working from their homes, often using their own personal devices connected to a shared home network.
To survive and thrive in this new cybersecurity landscape, organizations need to familiarize themselves with the most common cybersecurity risks they are likely to encounter and adjust their defenses accordingly.
This is especially true for SMBs because cyberattacks on their resources are growing in both frequency and severity. A single cybersecurity incident costs businesses of all sizes $200,000 on average, and that’s more than enough to force many financially stable small businesses to close their doors for good.
With all this in mind, let’s take a closer look at the five most common cybersecurity risks that are threatening SMBs in 2021 to help you understand what you’re up against.
1. Ransomware

At this point, ransomware is old news, but that doesn’t change anything about the fact that it remains the biggest cybersecurity risk.
One doesn’t need to look any further for evidence than the recent Colonial Pipeline cyber attack, which took down the largest fuel pipeline in the U.S. and forced its operator, Colonial Pipeline Co., to pay a $4.4 million ransom.
According to cybersecurity researchers from Infrascale, almost half of all SMBs have been targeted by a ransomware attack, and 73 percent of those SMBs that have been targeted actually paid a ransom.
In addition to following basic cybersecurity best practices, the most effective protection against ransomware is a robust backup and recovery strategy. When encrypted files can be sacrificed because they exist in one or more additional locations, then there’s one less reason to pay the ransom.
2. Attacks on Remote Employees
Remote employees don’t have it easy. They not only have to create a comfortable work environment for themselves and, in many cases, be their own IT support, but they also somehow have to defend themselves against a relentless onslaught of attacks, including phishing emails, vishing phone calls, password-based attacks, and more.
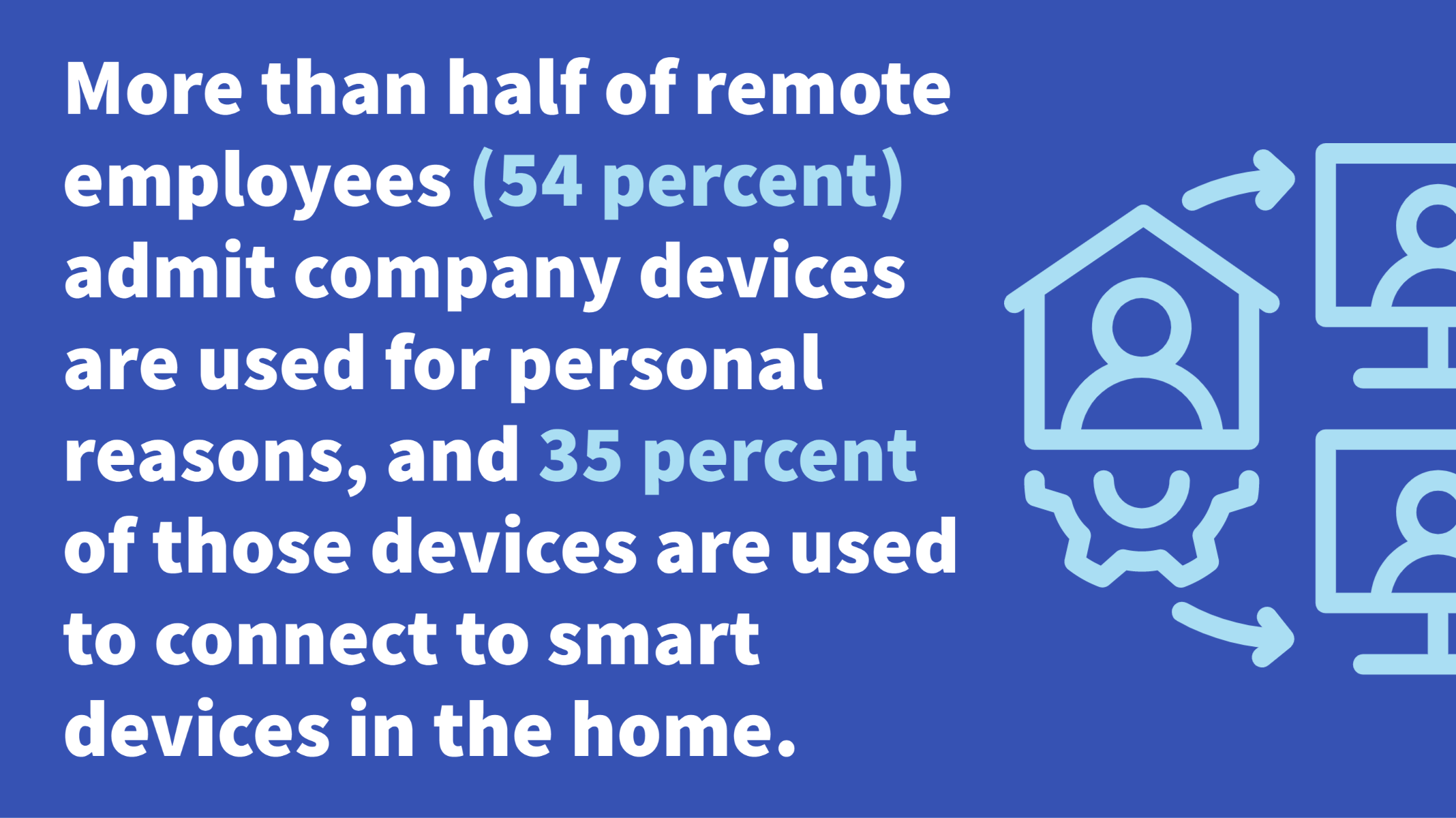
It then doesn’t help at all that more than half of remote employees (54 percent) admit company devices are used for personal reasons, and 35 percent of those devices are used to connect to smart devices in the home, according to AT&T research.
While not all organizations can equip their employees with company-issued laptops and smartphones, they can always invest in cybersecurity awareness training to educate them about the threats associated with remote work and the use of personal devices for work-related purposes. When combined with multi-factor authentication, a virtual private network, and other evergreen cybersecurity defenses, attacks on remote employees are much less likely to result in a costly data breach.
3. Cloud Computing Attacks
The COVID-19 pandemic is driving cloud computing adoption to new heights. In 2020, expenditure on global cloud infrastructure services surged by 33 percent, according to industry analyst firm Canalys.
Cloud computing can be especially beneficial to SMBs because it gives them access to cost-effective, scalable, secure infrastructure at a predictable monthly price and with no upfront expenses. However, these and other benefits are not without serious risks.
The cloud has quickly become a new vector for cyber attacks exploiting weak passwords, shared technology vulnerabilities, and weak cryptography. To avoid such attacks, it’s paramount to partner only with reputable cloud providers and update security policies to ensure the security of cloud-based solutions by enforcing the use of strong authentication mechanisms and data encryption.

4. Pharming Attacks
Pharming attacks are basically phishing attacks without a lure. Instead of relying on various social engineering techniques to trick unsuspecting victims into clicking on a malicious link, cybercriminals infect their victims with malware that automatically redirects them to bogus websites without their knowledge.
The ultimate goal of cybercriminals is to steal sensitive information, such as credit card numbers, passwords, and verification codes, and use this information for various nefarious purposes.
Pharming attacks, or at least the malware they rely on, can often be detected by antivirus and anti-malware security software with web browser monitoring capabilities, but users themselves should be trained to recognize its signs, such as when the address says “HTTP” instead of “HTTPS” in the address line.
5. Insider Threats

Some of the most common cybersecurity risks threatening SMBs and enterprises alike come from inside the organization. These so-called, and they can be separated into three categories based on their origin:
- Compromised insider threats: Employees that don’t realize they have been compromised.
- Careless insider threats: Employees that neglect basic cybersecurity practices.
- Malicious insider threats: Employees, sometimes former ones, that intentionally harm their organization by abusing their access credentials.
What makes insider threats especially dangerous is their hard-to-detect nature. Commonly employed cybersecurity defenses, such as firewalls and endpoint security tools, can’t reliably detect insider threats because their focus are threats coming from the outside.
To minimize the risk of insider threats, it’s important to implement and enforce strict password and account management policies and practices and watch out for common detection indicators of insider attacks, such as large data transfers, multiple failed logins, or incorrect software access requests.
The good news is that there are intelligent tools that make this fairly easy, and their implementation doesn’t require too much effort. If you need help with your cybersecurity services, feel free to contact us.

