Cybersecurity threats are becoming more sophisticated and varied, making it that much more difficult for businesses to protect their data. In the past, it wasn’t too difficult to prevent attacks. It was as simple as finding the right lock to the front door of your home. Today, however, protecting your digital assets requires a more strategic and layered approach.
If your goal is to create a more secure environment, protect your assets from cyber-attacks, and quickly recover in the event of a breach, we recommend a layered security approach.
By using multiple layers of defense, it will be easier to detect and prevent attacks at various stages, making it more difficult for hackers to penetrate your networks. Each layer of defense should complement and reinforce the others, creating a cohesive and complete security posture.
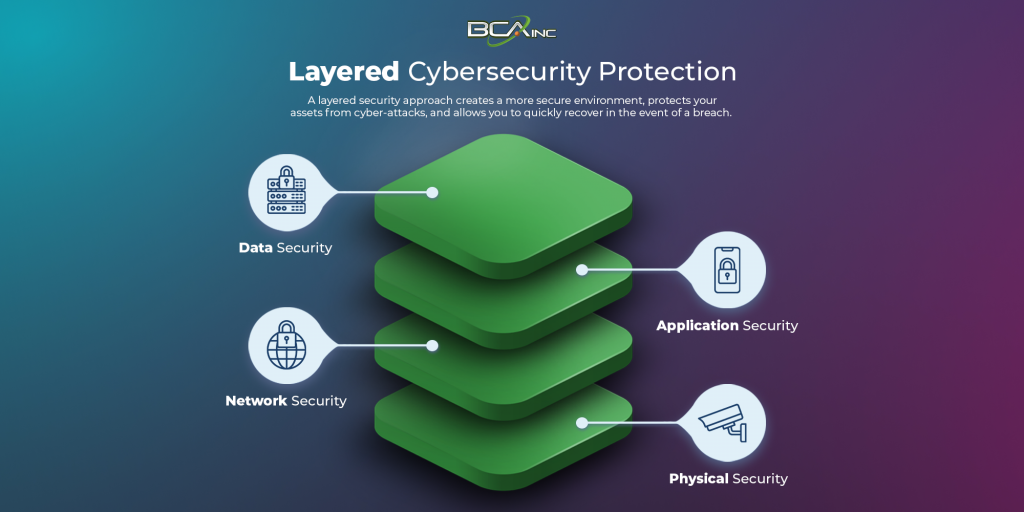
1. Physical Security
The first line of defense for your business against various forms of threats such as theft and vandalism. This layer consists of locks on doors and windows, using security cameras, and implementing access control systems. These measures will prevent unauthorized access to your premises and deter attackers from attempting to breach your security. In addition, alarm systems can notify law enforcement and security personnel in the event of an intrusion or suspicious activity.
If your business handles sensitive data such as personal identification information, financial data, and medical records, you must have these measures in place. If a breach occurs, it could lead to significant financial losses and legal consequences.
2. Network Security
This is an essential layer of defense that protects against a variety of threats, including malware, ransomware, and hacking attempts. It involves securing your business’s computer networks and systems from unauthorized access, misuse, and modification.
Network security measures include firewalls, intrusion detection and prevention systems, virtual private networks (VPNs), and encryption technologies. Firewalls will block unauthorized access to a network by filtering incoming and outgoing traffic. Intrusion detection and prevention systems (IDPS) can detect and prevent potential attacks, while VPNs provide secure remote access to networks. And encryption will ensure that sensitive information transmitted over the network cannot be intercepted and understood by unauthorized parties.
Not only can strong network security measures protect your valuable resources from unwanted intrusion, but it can also help your business comply with industry and regulatory requirements, such as the General Data Protection Regulation (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS).
It’s important to note that network security is not a one-time solution. It will require ongoing monitoring, maintenance, and updates to ensure that the security measures remain effective against new and ever-evolving threats.
3. Application Security
This layer focuses on protecting software applications from potential security threats. It encompasses a range of measures and best practices designed to identify and address vulnerabilities in software applications before they can be exploited by attackers.
Measures include authentication and authorization controls, input validation, error handling, and encryption. Authentication and authorization controls ensure that only authorized users have access to applications and data, while input validation helps prevent attacks such as SQL injection and cross-site scripting (XSS).
In addition to preventing attackers from exploiting vulnerabilities in software applications to access sensitive data or resources, application security can also help your business comply with regulatory requirements, such as the Health Insurance Portability and Accountability Act (HIPAA) and the Federal Information Security Management Act (FISMA).
Like network security, application security will also require ongoing testing, monitoring, and updates to ensure that security measures remain effective.
4. Data Security
This is crucial layer of defense focuses on protecting your data from unauthorized access, use, disclosure, modification, or destruction. It encompasses a range of measures and best practices designed to ensure that data is only accessible to authorized users and is protected from both external and internal threats.
Access control measures, such as permissions and passwords, are a key component of data security. They help ensure that only authorized users have access and can prevent unauthorized users from viewing or modifying it. Access control measures can also help track user activity and identify potential security breaches.
Encryption is another important aspect of data security. It can help protect sensitive data, such as financial information, health records, and intellectual property, from being intercepted or stolen by attackers.
Data backups are also critical in data security, as they can help ensure that data can be recovered in the event of a security breach or other disaster. In addition, regular data backups prevent data loss and ensure business continuity in the event of a cyber-attack or other data loss event.
Finally, data security also includes the proper disposal of data. When data is no longer needed, it should be securely deleted or destroyed to prevent it from falling into the wrong hands.
Layered Cybersecurity Protection With BCA IT
We know that implementing multi-layered cybersecurity measures can be costly and time-consuming but the costs of not doing so can be astronomical due to hefty fines and reputation damage. Therefore, investing in cybersecurity is a wise decision for any business, regardless of its size.
Choosing a reputable managed service provider like BCA can help you navigate the complexities of cybersecurity and ensure your business is adequately protected. While no one wants to think about being hacked, the reality is that it's not a matter of if but when. Taking proactive steps to prevent cyber-attacks is the best way to ensure peace of mind and protect your organization's sensitive data. For more information about multi-layered cybersecurity protection and specialized services, contact BCA today.

You must be logged in to post a comment.