Is your inbox suddenly overflowing with all kinds of subscription emails you never signed up for, making it extremely difficult for you to find messages from important senders? If so, it’s likely that you’ve become a victim of an email bombing attack.

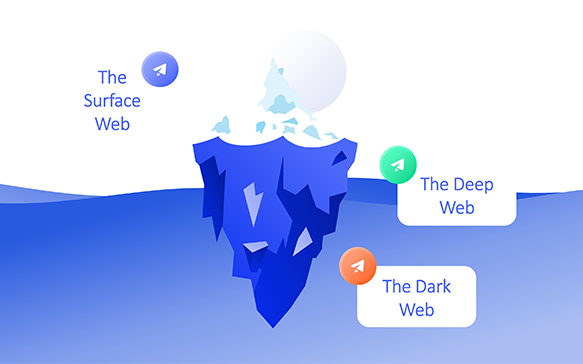
The Deep Web, the Dark Web, the Surface Web: What’s the Difference?
Hackers and dark forces are lurking in the dark depths of the web, but you may not know how deep they go. The dark web is a hidden network of websites only accessible through the use of specialized browser. It’s used for keeping internet activity anonymous and private, which can be helpful in both legal […]

What Was The Realtek Exploitation?
The Realtek SDK is used by many vendors to develop their products, and in recent days we have seen a large number of vulnerabilities being exploited. Realtek has been working with the affected vendors and patches are currently available for some Realtek chipsets that will close up these exploit vectors.
Best Antivirus Endpoint Detection & Response Software 2022
Endpoint detection and response is one of the best ways to protect your company’s data. But with so many endpoint detection software available, which should you choose? We have created a list for you that includes top 5 endpoint detection & response softwares in 2021. What is Endpoint Detection & Response Software? Endpoint Detection & […]

Spear Phishing: Cybercriminals Are Successfully Scamming SMBs
All organizations that will still be around in five years have at least a basic awareness of the threat posed by phishing, the fraudulent practice of sending seemingly legitimate emails to trick their recipients into revealing sensitive information or eliciting a certain action.

10 Cybersecurity Dos and Don’ts for Remote Employees
The global health crisis that paralyzed the entire world last year caused a massive shift to remote working as organizations tried their best to remain operational. Although the COVID-19 restrictions that prevented many employees from working from the office have largely been lifted, remote working is here to stay, at least to some extent.

Real-World Examples of Cloud Computing
Cloud computing is not just a buzzword anymore. It’s one of the fastest-growing industries in the world, expected to grow from $371.4 billion in 2020 to $832.1 billion by 2025. Examples of cloud computing can be found all around us because they make up the foundation of many organizations’ IT infrastructures.

Desktop as a Service (DaaS) Can Help SMBs Achieve Growth
Small and medium businesses are in a tough spot because they face many of the same challenges as larger enterprises while having just a small fraction of their resources. That’s why they’re constantly searching for cost-effective solutions capable of making their hectic lives just a bit easier.

5 Simple Ways to Improve Your Computer Performance in 2022
It’s astonishing how much computers have evolved over the last decade alone. But despite being more powerful and affordable than ever before, they still suffer from one annoying problem: they slow down over time. To be fair, they don’t slow down on their own.

5 Common Cybersecurity Risks Threatening SMBs in 2021
It took just one year for the cybersecurity landscape to change dramatically. As organizations large and small adapted to social distancing guidelines by embracing remote work arrangements as the new normal, cybercriminals shifted their sights to individual employees working from their homes, often using their own personal devices connected to a shared home network.
