Picture this: You're relaxing after a long day at work, perhaps sipping your evening drink, when suddenly your phone starts lighting up like a Christmas tree. You're flooded with push notifications, all screaming for attention - "Verify your login! Approve this! Confirm that!" The notifications become overwhelming. You just want them to stop. So, what do you do? You click ‘confirm’ because you just want it to end. Welcome to the world of MFA Fatigue.
Understanding Multifactor Authentication (MFA)
Before we can talk about MFA fatigue, we need to understand Multifactor Authentication (MFA). This security measure requires users to provide multiple pieces of evidence to prove their identity before granting access to a system. It's like a digital version of a physical security checkpoint where you must show multiple forms of identification before entering.
In cybersecurity terms, these pieces of evidence, or 'factors,' generally fall into two categories: something you know (like a username/password combination) and something you have (like a PIN code, smart card, or biometric factor such as a fingerprint).
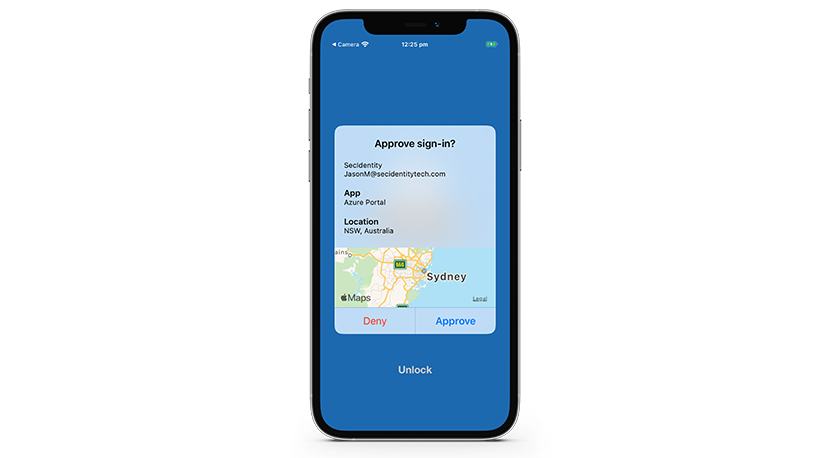
What is MFA Fatigue?
However, as with any solution, MFA isn't foolproof. MFA fatigue is a recent phenomenon, a unique vulnerability that has risen in parallel with increased MFA usage.
MFA fatigue, also known as authentication bombing or push spam, is a hacker technique aimed at exploiting the human element of the MFA process. In a typical MFA fatigue attack, hackers relentlessly bombard a user with MFA requests, hoping to wear down their patience and vigilance. Eventually, the user, annoyed or exhausted by the incessant notifications, may mistakenly accept a fraudulent request, allowing the attacker to bypass the MFA safeguard.
MFA fatigue has gained prominence recently due to the increasing adoption of MFA and the rise of remote work. With more employees logging in from various locations, the need for MFA has grown. However, this has also created an opportunity for hackers to exploit the MFA process through fatigue attacks.
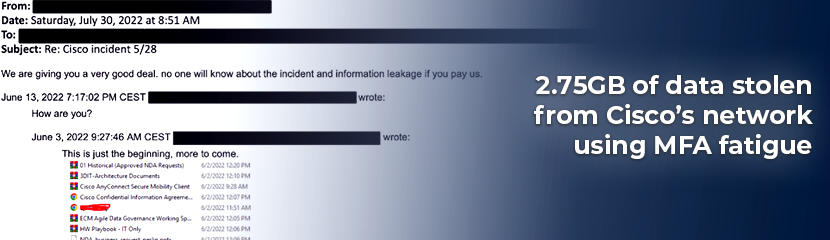
In May 2022, Cisco confirmed that a group of hackers known as Yanluowang got into their system. They did this by stealing a worker's login details. The hackers kept asking for extra security checks until the worker, fed up with the constant requests, finally agreed.
Once they got in, the hackers moved around to different parts of the system, getting more and more control as they went along. They put harmful software on the system that gave them even more access. Cisco found out about the attack and got the hackers out, but the hackers kept trying to get back in for several weeks.
Shielding Against MFA Fatigue: Effective Measures
Despite the worrying trend, all is not lost. There are multiple strategies to combat MFA fatigue and enhance your cybersecurity posture:
- Enable Additional Context: Make your MFA requests more informative. Include details like which account triggered the MFA notification, the location, and the device used for the login attempt. This context can help users distinguish between legitimate and fraudulent MFA prompts.
- Adopt Risk-Based Authentication: This feature adjusts security requirements based on known attack patterns, including repeated login failures and unusual login locations. It adds an extra layer of security, helping to combat MFA fatigue.
- Implement FIDO2 Authentication: FIDO2 provides password-less authentication and MFA based on biometrics, keeping your login credentials secure and reducing the risk of MFA fatigue.
- Disable Push Notification as a Verification Method: Replacing simple push notifications with verification methods like number-matching or time-based one-time passwords can prevent accidental approval of MFA requests.
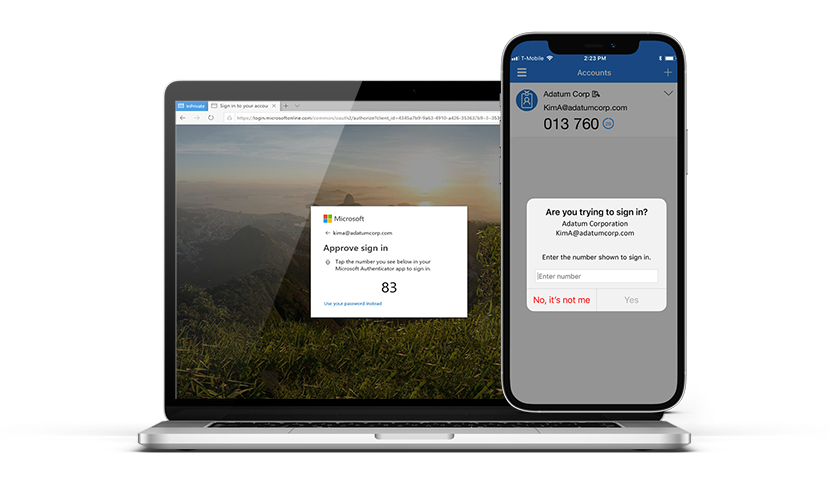
- Limit Authentication Requests: By capping the number of MFA requests allowed, you can reduce the risk of fatigue and deter hackers from using this tactic.
- Spread Security Awareness: Ensure all users understand the concept of MFA fatigue and the risks it presents. Regular cybersecurity training can go a long way in preventing such attacks.

While MFA fatigue presents a significant challenge, it can be prevented. With proper awareness, preventive measures, and a proactive approach to cybersecurity, individuals and organizations can effectively mitigate the risks associated with MFA fatigue. This is where BCA comes in. As an expert in providing customized IT solutions, BCA can help businesses fortify their security infrastructure, educate their staff about emerging threats like MFA fatigue, and devise strategic response plans. Contact us today!


You must be logged in to post a comment.